Nowadays, receiving suspicious emails is an all-too-common occurrence. These emails can range from phishing attempts to malware-laden attachments, posing serious risks to both individuals and businesses.
Nearly 1.2% of all emails sent globally are malicious, which translates to around 3.4 billion phishing emails being sent every single day.
So, what should you do when an email looks suspicious? One of the safest and most effective steps you can take is to analyze it in a sandbox environment before opening any attachments or clicking on any links.
Why You Should Analyze Suspicious Emails in an Isolated Sandbox Environment
Analyzing suspicious emails in a sandbox environment like ANY.RUN is a crucial step in protecting yourself and your organization from potential cyber threats. Here’s why:
- Watch in real time how the sandbox safely executes the attached files or links, revealing any malicious activity.
- Determine the specific damage the email could cause to your system, such as file encryption, data theft, or system compromise, without putting your actual network at risk.
- Uncover concealed malware, phishing attempts, or other malicious elements that might not be immediately visible.
- Conduct your investigation in a controlled, isolated environment, ensuring that any harmful actions remain contained within the sandbox.
- Use the insights gained from the sandbox analysis to decide whether to block the email, quarantine the attachment, or take other protective measures.
Analyze suspicious emails for free- Try now
Main Steps on How to Handle Suspicious Emails
When you receive a suspicious email, resist the temptation to open attachments or click on links. This is often how attacks begin. Instead, use a sandbox environment to safely analyze the attachments and determine whether they are malicious before taking any further action.
Here’s how you can check the attacked file or shared link:
1. Upload the attachment or paste the shared link
Use a sandbox tool like ANY.RUN to upload the suspicious attachments or copy and paste the links it contains.
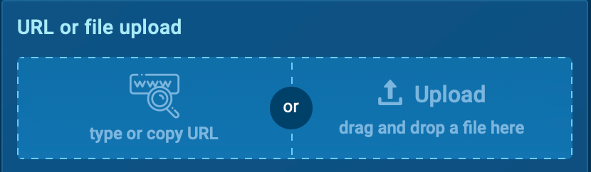
2. Configure the sandbox environment
Before starting the analysis, you can configure the sandbox settings to create a virtual environment that closely mimics your actual system.
This allows you to handle and examine the suspicious email as if it were on your own machine, without risking any real damage to your system.
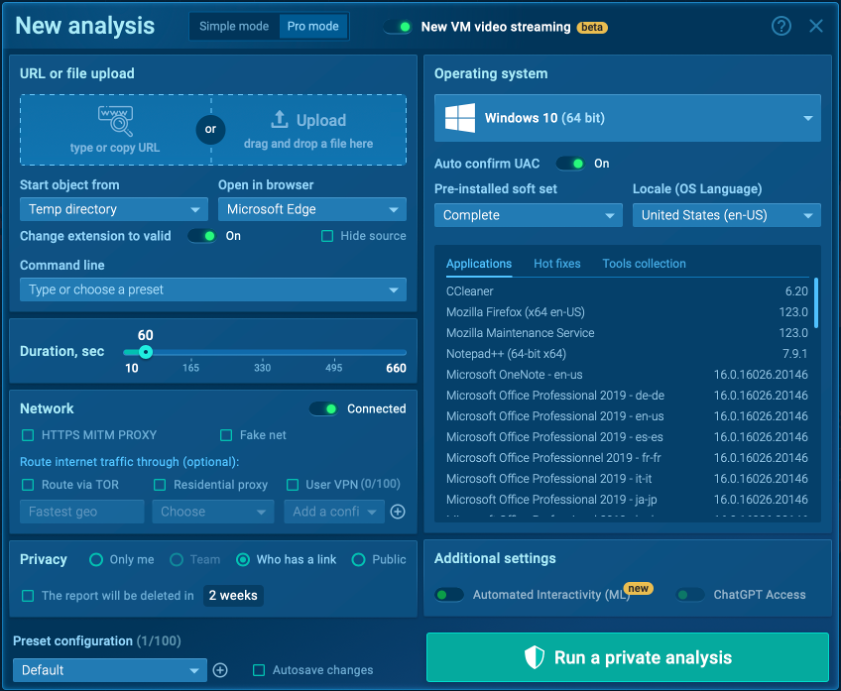
By replicating your environment in the sandbox, you can see how the attachments would behave in your real setup, ensuring a more accurate and secure analysis.
3. Run the malicious element in the sandbox
Once the settings are ready, run the analysis. Now you can observe how the email or attachment behaves in the sandbox.
Look for any signs of malware, such as attempts to modify system files, communicate with external servers, or install software without permission.
You can easily interact with the file, perform actions inside the virtual environment to see how the file or link behave.
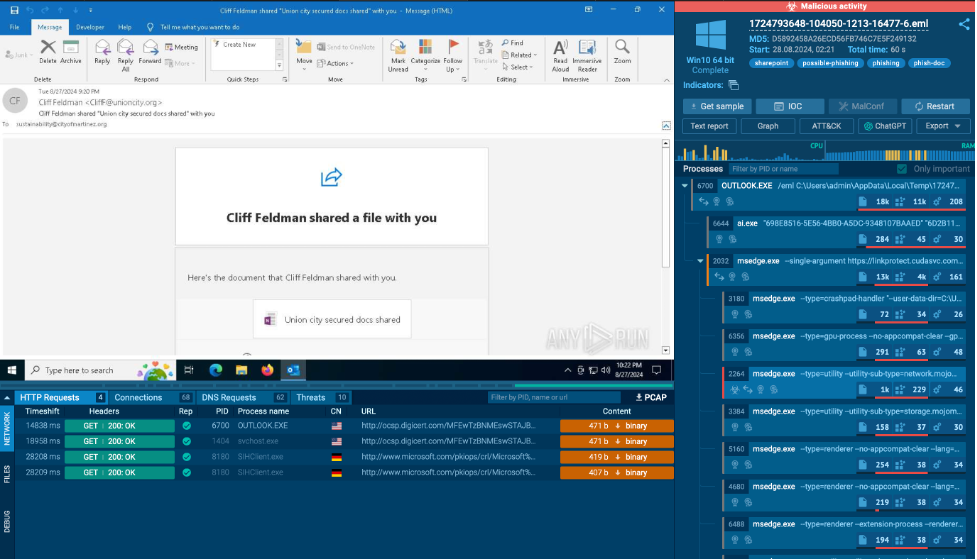
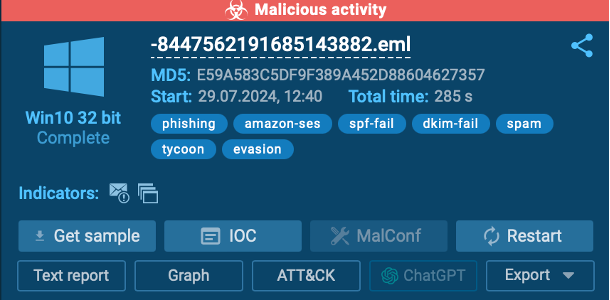
4. Review the Sandbox Report
After the analysis, the sandbox will generate a report detailing the email’s behavior. This report will help you determine whether the email is safe or if it’s a threat.
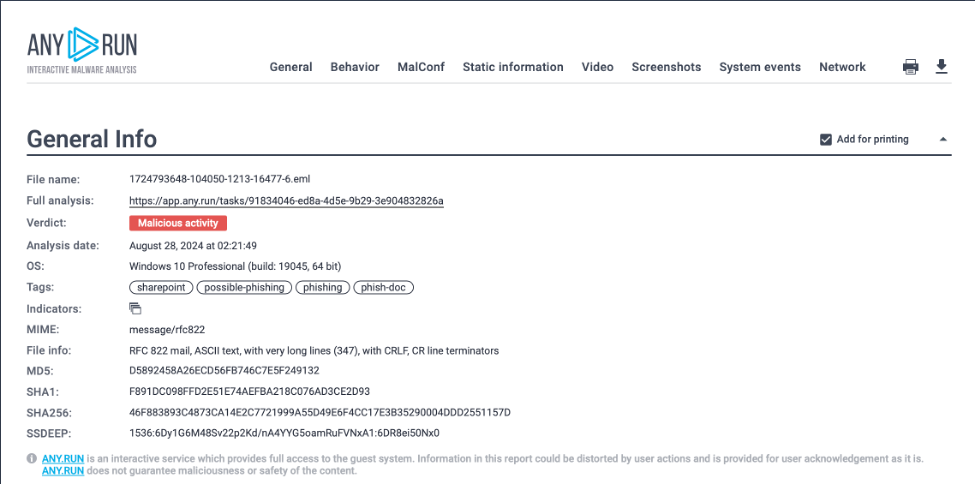
Additionally, keep an eye on the top right corner of the screen during the analysis. Any detected malicious activity will be displayed there, along with detailed information about potential threats.
This user-friendly feature is especially beneficial for those who aren’t tech-savvy, allowing you to quickly identify and assess risks as they emerge.
5. Take actions based on the finding
After the analysis is complete, carefully review the results provided by the sandbox. If the email or its attachments are identified as malicious, take immediate action to protect your system:
- Delete the email: Remove the email from your inbox and trash folder to prevent any accidental interaction in the future.
- Report the threat: If you received a suspicious email on your work email, it’s crucial to notify your IT department or a cybersecurity professional immediately. Provide them with a detailed sandbox report, which will help them conduct a broader security assessment and take necessary precautions to protect your organization.
- Update security measures: Consider updating your antivirus software, spam filters, and other security settings based on the findings to prevent similar threats in the future.
- Educate yourself on the matter: Take this opportunity to educate yourself on the matter by reflecting on the steps you took and the analysis results. Understanding these processes will help you be better prepared to handle similar threats in the future.
Expose Suspicious Emails in Minutes
Don’t leave your digital security to chance. Use ANY.RUN’s interactive sandbox to analyze suspicious emails, uncover hidden threats, and protect your system with confidence.


